I suppose the main difference is that with nomadic identities, you can send a message to ANY of the clones*, and the recipient will get it since they are all synced. With portable identity, you must send the messages to the current domain, or else they won’t be received.
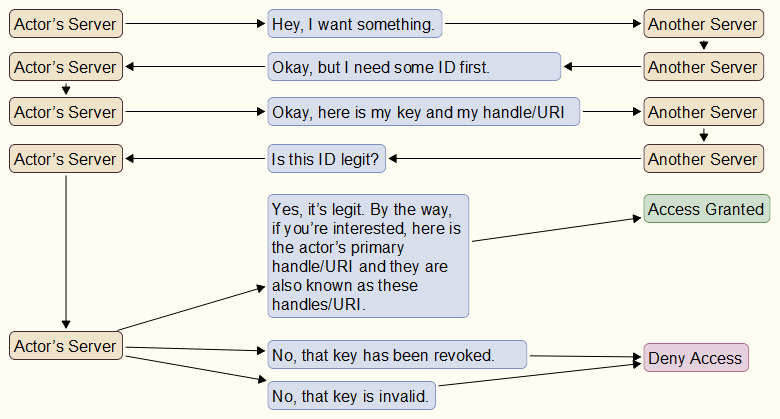
From an ActivityPub perspective, ActivityPub doesn’t actually care how identities are managed on each platform. They could use DID documents as specified in the DID standards, or they can use something like Zot to manage the identities. ActivityPub wouldn’t actually care about how a platform does it. ActivityPub just wants you to send the correct information as defined in FEP-c390.
If ActivityPub (or more accurately, the platforms that accept FEP-c390 messages) consider different actors with the same key to be the same person, then that is an implementation of nomadic identity. If they do not consider them to be the same person, then they haven’t implemented nomadic identity.
i.e. user43@example.social and user42@example.org are the same person since they have the same key or unique identifier.
The reason why I mentioned adding multiple aliases is that there are two use cases that would benefit from this:
- Nomadic identity / any clone can accept the message*; (primary or sending to all is preferred).
- Backup servers / other servers can accept the message if the primary is down.
It basically works like an MX record for email. Here are a list of servers that can accept messages for this email address. Basically, this is the same exact thing, except with fediverse messages and it allows multiple handles for the same identity.
*The Zot specification says you should send the message to all of the clones, but realistically, since they are all synced, the message will still propagate to all clones if you send the message to one clone, it’ll just be slower.
But, you are right. They are very similar, and there are only subtle differences, as long as you accept messages from any domain for a specific key.
A problem only arises if a platform refuses to accept the key (or messages with that key) because it comes from the “wrong” domain.