helge
December 10, 2024, 10:25am
1
Hi Folks.
This is about rights to configure
I currently have rights to neither settings. If I wanted to add something like Automate the create_readme script and issue creation, I would need these rights.
Do we have a process on who has these rights? On how to obtain them?
If yes, could we define one. Also could I have them? If yes, I would write the automation for the above step.
3 Likes
It’s informal. Initially only @aschrijver and @weex had those rights, now I have them too.
I added you to the administrators team. Can you access repository settings now?
3 Likes
helge
December 11, 2024, 10:09am
3
Thanks. I’ve now created:
Note at @fediverse/FEP-Editors
- Once this is merged please check it does the right thing.
- If you are ok with automating these things, I'll update the description of a facilitators role to just be checking and mergin
- finally, can we rename the...
This should automate most FEP facilitators tasks.
2 Likes
helge
December 20, 2024, 8:10am
4
cc @fep.hosts
Just so that everyone is informed.
1 Like
helge
January 20, 2025, 11:26am
5
I’ve merged the pull request. Getting it to work was harder than expected. A bug in the configuration arose due to one needing the private key in CI ending in a new line.
1 Like
helge
January 20, 2025, 12:24pm
6
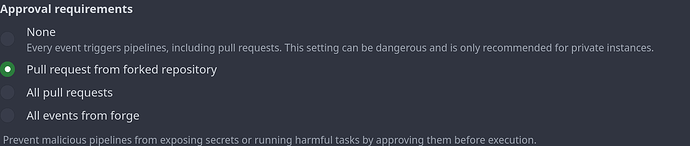
Another thing, I just discovered
this means that currently, we need to approve the CI job if somebody submits a FEP. Is this the state we want?
Link to woodpecker settings: Woodpecker
Is manual approval required for every CI job, including on-push checks? In this is the case, I would prefer to not have it, because in my opinion automatic on-push checks have greater utility.
helge
January 21, 2025, 8:23am
8
I changed it to no permission for now.
If there are any effects, please comment here.
No issues so far.
What are the consequences of changing it to no permission? The description says “This setting can be dangerous and is only recommended for private instances .” But what do they mean by “dangerous”?
helge
January 22, 2025, 6:39am
10
I didn’t research woodpecker’s thinking. However, my understanding is:
Woodpecker keeps secrets, e.g. the deploy key to update the FEP repo.
You can give pull request jobs access to secrets.
So people can access to these secrets using appropriate pull requests.
So as long as we limit access to secrets to jobs triggered by “push” and “tag”, we are fine.
1 Like
I’ve just submitted a new FEP, everything is working as expected . Good job!
1 Like
helge
February 7, 2025, 10:10am
12
Is there any objection to autogenerating the discussions link the issue? It should be available from the discussionsTo link in the FEP.
See #487 - [TRACKING] FEP-a974: All Actor types should be followable - fediverse/fep - Codeberg.org
1 Like
No objections.
<random text because discourse requires comment to have at least 20 characters>
1 Like
how
May 13, 2025, 7:53am
15
Thank you @helge and @silverpill for making it a transparent collective process.
2 Likes
helge
September 21, 2025, 7:09am
16
In #22 - [TRACKING] FEP-1b12: Group federation - fediverse/fep - Codeberg.org , I commented about my desire for code blocks in FEPs having highlighting, e.g. using
```json
{
"type": "AnimalSound"
}
```
instead of the option without json.
We could automate this type of checks with a markdown linter.
A Node.js style checker and lint tool for Markdown/CommonMark files.
leads to about 2000 errors, which could be reduced by automatic fixing and disabling some rules to about 160.
Should we work towards enforcing such a concept of linting?
1 Like
No, linter shouldn’t block proposals.
Optional linting is fine.
1 Like